Routing all remote traffic through OpenVPN
There’s a great guide on OpenWRT.org that covers most of what I wanted to do. However, I ran into a few snags and figured this might help someone else.
My goal was to do the following:
- Set up an OpenVPN running on my DD-WRT/OpenWRT compatible router
- Configure a Windows 7/8 laptop to connect to the tunnel for the following reasons:
- Default route all traffic through the router in hopes of protecting traffic when on public networks
- Access “local” resource while out on the road
DD-WRT vs. OpenWRT
I’ve tested OpenVPN on a Linksys E2000 running DD-WRT and had good luck with it. I also have a TPLink 4300 which runs DD-WRT, but I had trouble getting SSH to work (the option was greyed out) and ultimately could not get OpenVPN to run. So I decided to try OpenWRT instead. For my needs, I much preferred OpenWRT and the steps here are geared for OpenVPN running on OpenWRT.
OpenWRT
192.168.0.x and 192.168.1.x are very commonly used and could cause some problems when you are connecting to various routers and public networks.
Once you have OpenWRT installed on your router, I suggested that you change the default LAN IPs to be something other than 192.168.1.x. For this tutorial, I have changed the IPs to be 192.168.99.x. So when you see .99. then just replace it with whatever you configured the router to use.
OpenVPN Server Installation and Configurations
Turn on SSH
You may need to enable SSH access before you can log in. To do so go to System -> Administration
Then scroll down to the section that says SSH Access and make sure the settings are enabled:
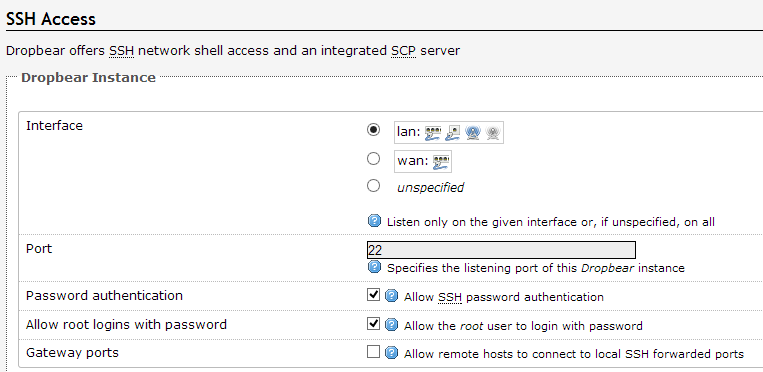
Install the OpenVPN and SFTP Packages
SSH into your router by going to 192.168.99.1 using the SSH Port that you set above. The default is 22. Sign in as root and use the password that you have set to sign into your OpenWRT admin website.
Once you are signed in, you can run the following commands. There is no need to change the directory/path that you are in.
This will run a command line update:
opkg update
This will install the OpenVPN and Easy RSA (for generating the keys):
opkg install openvpn openvpn-easy-rsa
This will install SFTP (FTP over SSH) which is useful when you want securely to copy the keys off the server and onto a client:
opkg install openssh-sftp-server
The OpenWRT guide suggested that you can install the GUI package (luci-app-openvpn), but this failed for me using the latest build of OpenWRT saying that the package could not be located. This package is not needed in order to get things working.
Building the Certificates/Keys
Changing defaults (optional)
When generating the keys, you will be prompted for a lot of settings. You can change some of these default values in order to make the prompts easier. That is, you can just press [enter] for the defaults.
So, to help make some of the prompts easier, you can edit this file. Towards the bottom are some of the defaults:
vi /etc/easy-rsa/vars
Get your server/keys ready:
Next run the following:
clean-all
build-ca
build-dh
Next build the server keys:
build-key-server server
This will give you a lot of prompts. I tried to keep the answers here similar across the server and client keys, though you will need to keep the file names and common-names unique. That is you can’t have two client keys called “user1”
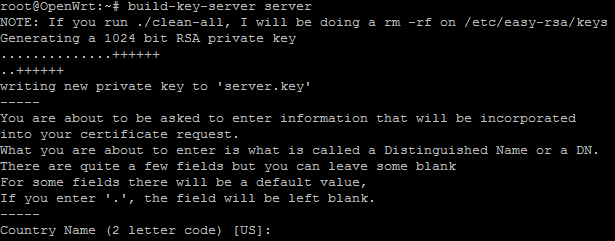
Note, when asked for a challenge password I put a randomly generated one in there. This did not seem to come up anywhere else or cause any problems.
Get your client keys ready:
I used the PCKS12 format. This format combines all the keys you need for the client to connect into one .p12 file. This would be the only file that you would need to ship to each client.
build-key-pkcs12 user1
Note, make sure you keep the Common Name unique. I just left it as user1 to match the file names.
Also, you can put an export password on this .p12 key which means that the client would have to enter this password anytime they connect or use the key. This password is optional and you can choose to leave the export password blank.
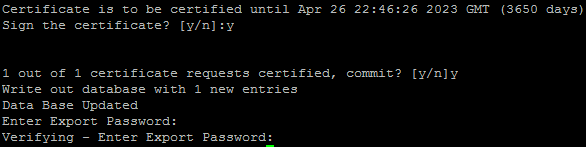
Copying the keys over
The keys that you are generating will be stored int he /etc/easy-rsa/keys folder. You will need to copy the server keys over to the /etc/openvpn/ folder for use with OpenVPN:
cd /etc/easy-rsa/keys
cp ca.crt ca.key dh1024.pem server.crt server.key /etc/openvpn/
OpenVPN Server configuration
Edit the OpenVPN Server configuration:
vi /etc/config/openvpn
Replace the server config with the following:
config 'openvpn' 'lan'
option 'enable' '1'
option 'port' '1194'
option 'proto' 'udp'
option 'dev' 'tap0'
option 'ca' '/etc/openvpn/ca.crt'
option 'cert' '/etc/openvpn/server.crt'
option 'key' '/etc/openvpn/server.key'
option 'dh' '/etc/openvpn/dh1024.pem'
option 'ifconfig_pool_persist' '/tmp/ipp.txt'
option 'keepalive' '10 120'
option 'comp_lzo' '1'
option 'persist_key' '1'
option 'persist_tun' '1'
option 'status' '/tmp/openvpn-status.log'
option 'verb' '3'
option 'server_bridge' '192.168.99.1 255.255.255.0 192.168.99.200 192.168.99.219'
option 'push' 'redirect-gateway def1'
list 'push' 'dhcp-option DNS 192.168.99.1'
Notes
- option ‘push’ ‘redirect-gateway def1’ – will instruct the clients to push all traffic through the router. This is what I wanted as one of my goals was to “encrypt” traffic from the client when connected to public networks. If you leave this option off, your clients will still be connected to the network and have access to local resources, but their default gateway may still be their outside network.
- list ‘push’ ‘dhcp-option DNS 192.168.99.1’ – will tell the router to push the DNS server (itself) down to the client. I ran into some trouble where the client could not resolve DNS without this command.
Start the server
Start server from Command line
/etc/init.d/openvpn start
If needed, you can also stop or restart the service:
/etc/init.d/openvpn stop
/etc/init.d/openvpn restart
Enable the OpenVPN server so that it automatically startup on boot.
/etc/init.d/openvpn enable
This can also be done via the OpenWRT GUI through System —> Startup and then clicking Enable next to OpenVPN:
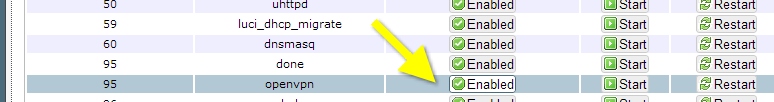
Router Network Configuration
Now that you have your server configured and started, the network/interface should show up and can be bridged. Using the OpenWRT web management, go to WRT —> Network —> Interfaces —> Edit LAN
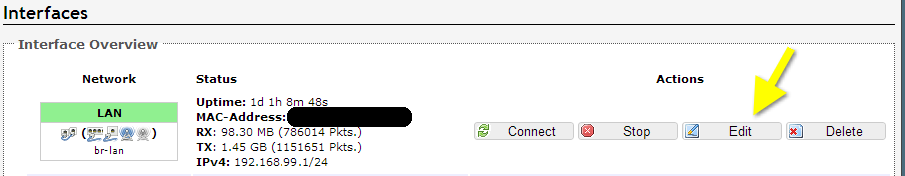
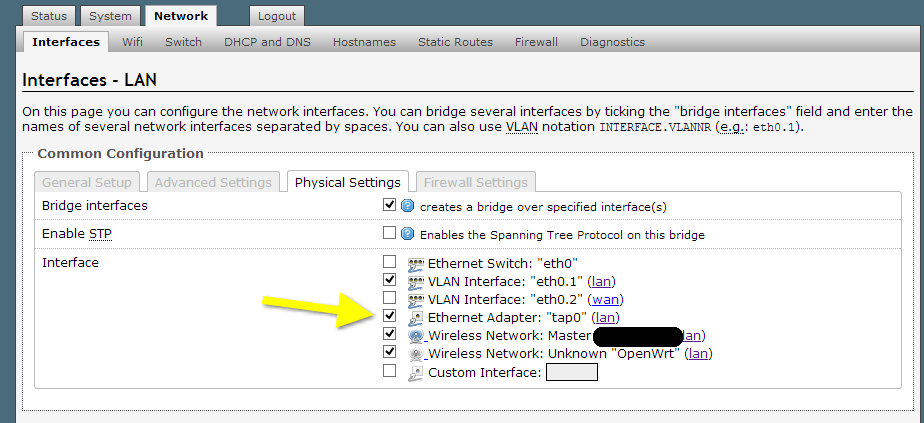
Then click on Physical Settings and check the box next to the tap0 interface in order to bridge that network. This essentially means that when someone connects to the tap0 (your OpenVPN network), they will have access to the other resources on the LAN, WLAN, etc.
Firewall and DHCP
Back to the SSH console for the next changes.
Update the firewall to allow Port 1194 UDP traffic.
vi /etc/config/firewall
Add the following to the bottom of this file:
config 'rule'
option 'target' 'ACCEPT'
option 'dest_port' '1194'
option 'src' 'wan'
option 'proto' 'tcpudp'
option 'family' 'ipv4'
Restart the iptables based firewall:
/etc/init.d/firewall restart
Next let’s update the DHCP ranges:
Initially I understood the DHCP changes incorrectly. The original configuration had 50 and 200 for the DHCP. I though it meant that the DHCP LAN should start at 50 and run through 200. However the second command limit means that the DHCP would be starting at 50 and run for 200 addresses thus ending at 250. If you remember from our OpenVPN configuration (above), we configured the OpenVPN clients to receive addresses from ~200-220. We don’t want this to overlap, so the settings must be changed to something like the above which says: Start at 50 and run for 150, giving a normal LAN DCHP range of 50-200.
vi /etc/config/dhcp
Change the LAN section to something like the following:
config 'dhcp' 'lan'
option 'interface' 'lan'
option 'ignore' '0'
option 'start' '50'
option 'limit' '150'
restart dnsmasq:
/etc/init.d/dnsmasq restart
To review:
- 50-200: LAN/WLAN address lease range
- 201-220: OpenVPN address lease range
Connect your clients:
Now that your server is up and running, let’s try connecting one of your clients. You need three things on the client to do this:
- Client must have OpenVPN client installed (Download here)
- The client configuration file must exist that matches the server and points to the right outside IP of your router
- The server key/certificate that we created above (we are using the .p12 format for this tutorial)
Client Config File (.ovpn)
Note, you may need to l launch notepad.exe with administrative privileges in order to write to the above folder. Alternately, you can create it somewhere else and then copy it in (where you will then need to grant admin privileges to copy).
Once you have the OpenVPN client installed, create a configuration file. On my Windows 7/8 instance, this file would exist in
C:\Program Files\OpenVPN\config\
In this path, use notepad.exe (or equivalent) to create a file called OpenWRT.ovpn
In this file put the following:
#Configuration
remote <your.server.address.here> 1194
client
tls-client
dev tap
proto udp
remote-cert-tls server
resolv-retry infinite
nobind
persist-tun
persist-key
pkcs12 user1.p12
comp-lzo
verb 3
On line 1, make sure you update to your servers outside WAN IP address.
Validating the Server/Keys
WARNING: No server certificate verification method has been enabled. See http://openvpn.net/howto.html#mitm for more info.
remote-cert-tls server – this line is required or else you will receive a warning in the log about MITM attacks. This warning is telling you that if you don’t validate the servers authenticity somehow, then someone could hack/attack your “secure connection” using a man-in-the-middle attack. This line asks your client to authenticate/validate the server keys first and should remove that warning.
Client certificate/key
This is the file that you created back in the SSH session on the OpenWRT. For this tutorial we are using the PKCS12 format which means all the keys are combined into a single file. You’ll need to copy your user1.p12 file from the OpenWRT server to the same path as the client configuration file that we just created (C:\Program Files\OpenVPN\config\).
One of the first steps that we did was to install the SFTP server onto your OpenWRT router. This will allow you to securely login and copy the file out. I used a program called FileZilla to do this.
Once you have the file in the right place, you should be all set to connect.
Connecting for the first time
Run the OpenVPN GUI which will put a little icon into your taksbar that has two red-monitor screens. Right click on this and select “connect”
Note, if you have more than one connection, then you will see them listed here and you would select one of those first, then select connect.
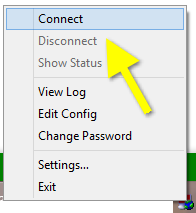
When you connect, a status screen will show up that will have a lot of log information. If you have an export password on your .p12 file, then you will see a prompt for that here.
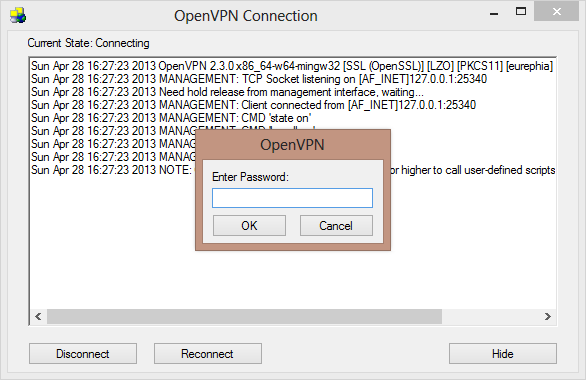
Once you successfully connect, the monitor lights will turn from red to yellow and finally to green and that should mean you are all set.
Testing 1…2…3…
You should be able to connect to the VPN even if you are connected behind the OpenWRT router. However, in order to properly test things out, you should really try connecting from an outside network (coffee shop, etc.).
Once you get the green light on the OpenVPN GUI, try some of the following tests.
Open WRT Management Web
Try to connect to http://192.168.99.1/ (or https://192.168.99.1/ if you have that turned) on. If you successfully see the login screen, then that means your VPN is working and you have access to your local resources. If you disconnect the VPN, you should not longer be able to access the management site.
tracert
First, let’s test this with the VPN connection off. So make sure the OpenVPN lights are red and you are disconnected.
In Windows, open up a command prompt (cmd) and type in:
tracert www.google.com
and then watch the results. You really only care about the first few lines.
You should now see a set of hops showing that you are routing through the network you are connected to (coffee shop, etc.).
Next, connect to your VPN. Once you have green lights and can get online, run the same command again. You want to see something like the following:
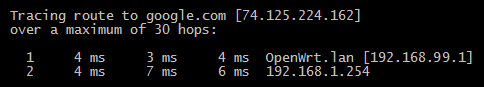
Notice that the first hop is your OpenWRT router at 192.168.99.1. The second hop should be whatever network your OpenWRT router uses to connect out. For testing, I had my OpenWRT router behind another network that ran off 192.168.1.254. Note: If you are running behind another router/firewall, you will need to open port 1194 on the “outside” firewall and point it to the OpenWRT’s LAN address on that network. This type of setup may be common for those plugging in behind an “all in one” Cable Modem/Router/Switch.
If you don’t see any difference in the tracert, but can successfully see local resources, that could mean that your VPN is connecting okay but not acting as the secure default route of all our traffic. Ensure that the setting: option ‘push’ ‘redirect-gateway def1’ is properly configured in the OpenVPN configuration file.
“What is my IP” test
As a final test. go to google and type in “what is my ip” and see what address it gives you. This should give you the outbound WAN address of whatever network your OpenWRT is connected. What this means is that when you visit websites, they are “seeing” you as though you are coming from the OpenWRT connected network and not the one you are directly connected to (coffee shop, etc.).
Comments?
Hope this guide sheds some additional light on configuring OpenVPN on an OpenWRT router. If you have any questions or suggestions, please leave them in the comments below.

 Frog is Wrong
Frog is Wrong